Collaborative Discussions
My posts for collaborative discussions

My posts for collaborative discussions
References:
1. https://owasp.org/www-project-top-ten/
2. https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure
3. Piętka K., (2018) [online] Bezpieczeństwo aplikacji internetowych. Available at: https://devpark.pl/pl/ataki-sieciowe-wedlug-owasp-najpopularniejsze-typy/ [Accesed on 22. 06. 2022]
4. Lazar, D., Chen, H., Wang, X., Zeldovich, N., (2014) Why does cryptographic software fail? A case study and open problems, Proceedings of the 5th Asia-Pacific Workshop on Systems, Beijing, China.
5. https://code-maze.com/owasp-top-10-sensitive-data-exposure/
6. Shankdhar P., (2013) [online] Protect Data by Preventing Insecure Cryptographic Storage. Available at: https://resources.infosecinstitute.com/topic/protect-data-by-preventing-insecure-cryptographic-storage/ [Accesed on 22. 06. 2022]
7. Schneier, B. (1998) Cryptographic design vulnerabilities, Computer, Vol. 31 (9): 29-33.
The answer for tutor comment:
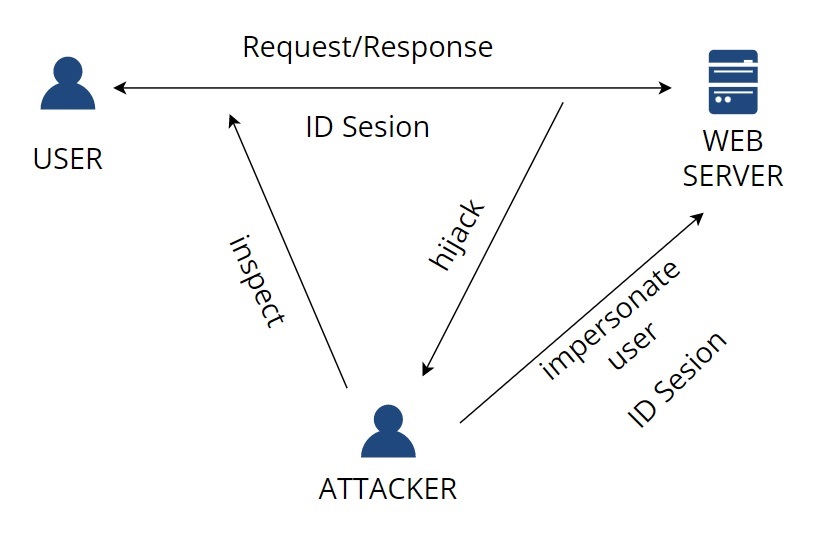
This type of hijacking is session sniffing. It's one of the most basic techniques for session hijacking. The attacker can use a sniffer, for example, Wireshark (which is an analyser that usually helps with troubleshooting of network). Because of that, the attacker can capture the session ID between a user and a server during a traffic network. As soon as the attacker gets the valid ID, can use it for unauthorized access. I learnt that there are three types of sniffing attacks: a) Wireless sniffer - dedicated to capturing data on wireless network b) External sniffer - in this approach both inbound and outbound traffic from an external locality to a web server, are monitored to collect information about the server. c) Internal sniffer - created for extracting information from the internal co-operate network. The attacker makes a machine vulnerable on the internal network and runs the sniffer to capture the data.
References:
1. https://www.venafi.com/blog/what-session-hijacking
2. https://owasp.org/www-community/attacks/Session_hijacking_attack
3. B. Prabadevi, N. Jeyanthi (2018) A Review on Various Sniffing Attacks and its Mitigation Techniques, Indonesian Journal of Electrical Engineering and Computer Science, 12, (3): 1117-1125.
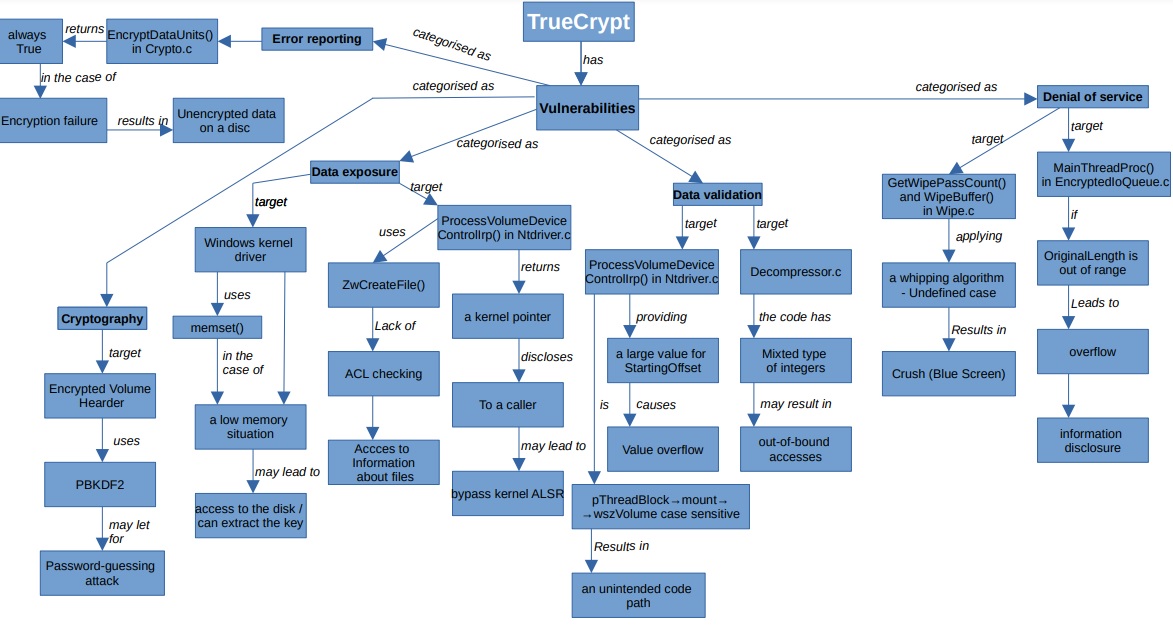
Even though the cryptanalysis OCAP for TrueCrypt did not find any evidence for serious security issues like a backdoor, they still underlined some problems that might be concerning in the case of using this open source encryption software in a secure way. OCAP for TrueCrypt consists of two parts: The first referees to the TrueCrypt bootloarder and Windows kernel driver, coding standards and performance. The second was about encryption in general. The auditors found eleven vulnerabilities: four medium severity, four low severity and three informational. The main issues with TrueCrypt are as follow:
a) The report said that “The bootloader and the Windows kernel driver did not meet expected standards for security code”.
b) The software did not meet good programming style, lack of comments and usage of old functions that did not meet security standards.
c) The code used old and not supported tools that might have put an operating system on a risk of malicious modification, unknown and unsupported modification.
d) The most dangerous issue is probably a weak volume header key derivation algorithm. The authors applied a standard key derivation algorithm PBKDF2, which uses an iteration count that is not big enough to prevent password-guessing attacks.
The analysis showed that there are some medium or low-security issues, however, it did not discourage from using TrueCrypt (Ritter 2014). However, in my opinion, they clearly presented issues that needed corrections immediately to keep users’ computers safe. Would I recommend using TrueCrypt to a friend? Of course not. Why? There are two main reasons:
1) This’s discontinued and unsupported encryption software, which means it’s unsafe.
2) Two principal vulnerabilities have been found. They do not allow for a backdoor, but they allow for malware installation that could result in figuring out description key of the software and other sensitive data (CVE-2015-7358, CVE-2015-7359).
Ontology graph for TrueCript
References:
1. Ritter, T., (2014) [Online] "iSEC Completes TrueCrypt Audit" available at: https://isecpartners.github.io/news/2014/04/14/iSEC-Completes-Truecrypt-Audit.html [Accessed on 03. 08. 2022]
2. Jain, K., (2015) [online] "TrueCrypt Encryption Software Has Two Critical Flaws: It's time to Move On" Available at: https://thehackernews.com/2015/09/truecrypt-encryption-software.html [Accessed on 03. 08. 2022]